“Here come’s a (New) Challenger”
Azure or Entra for the new generation is a big playing field, I’ve been writing a tool for Azure Engagements the entirety of 2025, now that we enter a New Year I decided to battle test the framework to see if it can withstand real world scenarios. We are engaging with the following scenario:
Your red team is on an engagement and has successfully phished a Mega Big Tech employee to gain their credentials. So far increasing access within Azure has reached a dead end, and you have been tasked with unlocking further access. In scope is the entire on-premises and cloud infrastructure. Your goal is to gain access to customer records and demonstrate impact.
PWNED Labs has already provided a walk-through for this scenario. We will follow the provided guidance and evaluate whether ANIMO produces the same results that would be expected during a real world engagement.
The first step is to verify the license assigned to the target user. Validation confirms that a Microsoft 365 license is present.
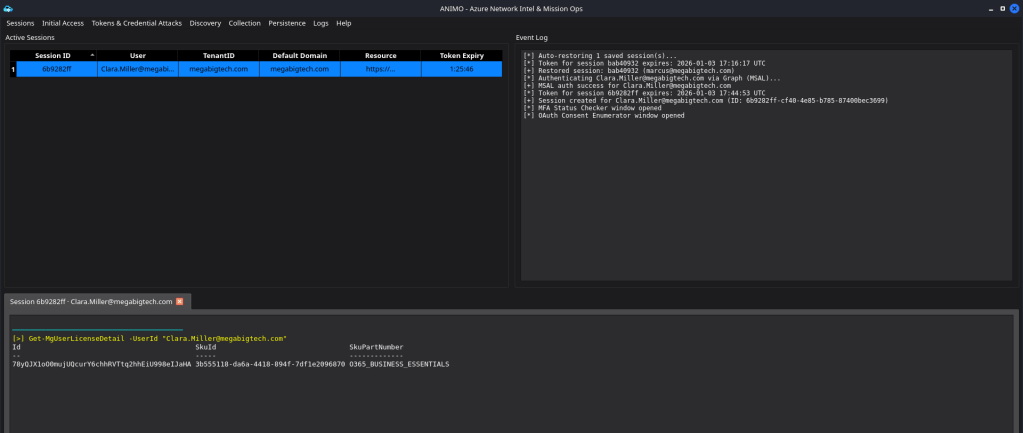
This confirms that the user has access to multiple Microsoft 365 resources, including Outlook, Teams, SharePoint, and other productivity services. We can continue leveraging ANIMO modules to further enumerate these resources.
The next focus is SharePoint. Within the ANIMO Collection menu, several modules are available that allow us to validate token permissions and determine whether the granted scopes permit access. In this case, the token provides sufficient privileges to utilize all Collection modules. While browsing SharePoint, we identify several files of interest.
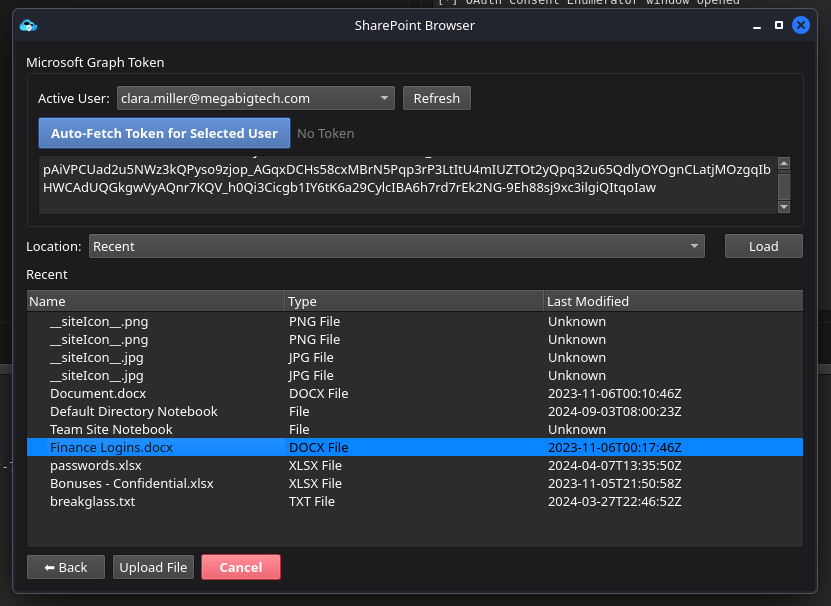
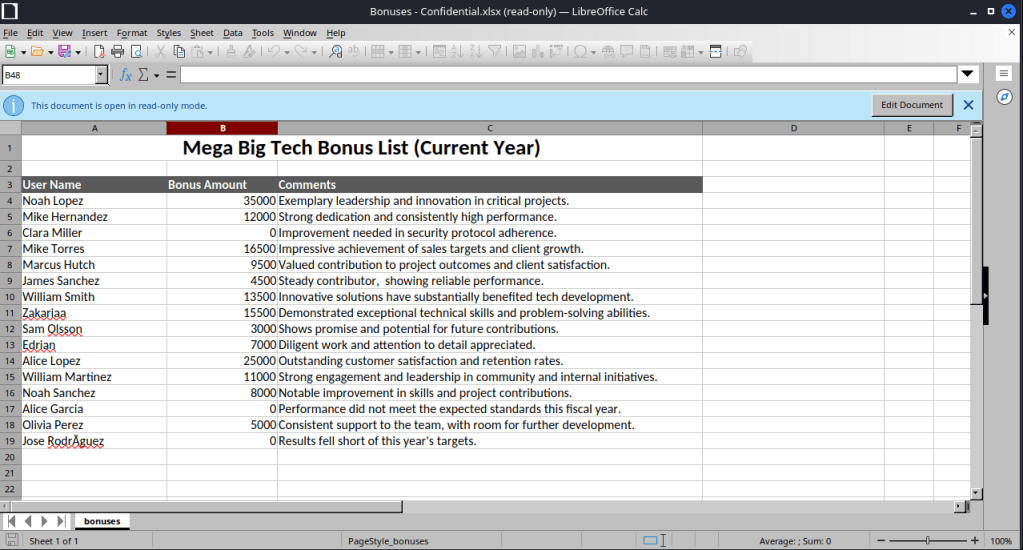
Progress is steady. We have identified files that contain user credentials. One of these files, titled Bonuses Confidential.xlsx, is password protected. At this stage, we have several viable options. We can attempt to recover the password through offline cracking, continue reviewing internal documentation for potential references to the password, or engage in user level reconnaissance by reviewing conversations and communications to identify any mention of password usage or reuse.
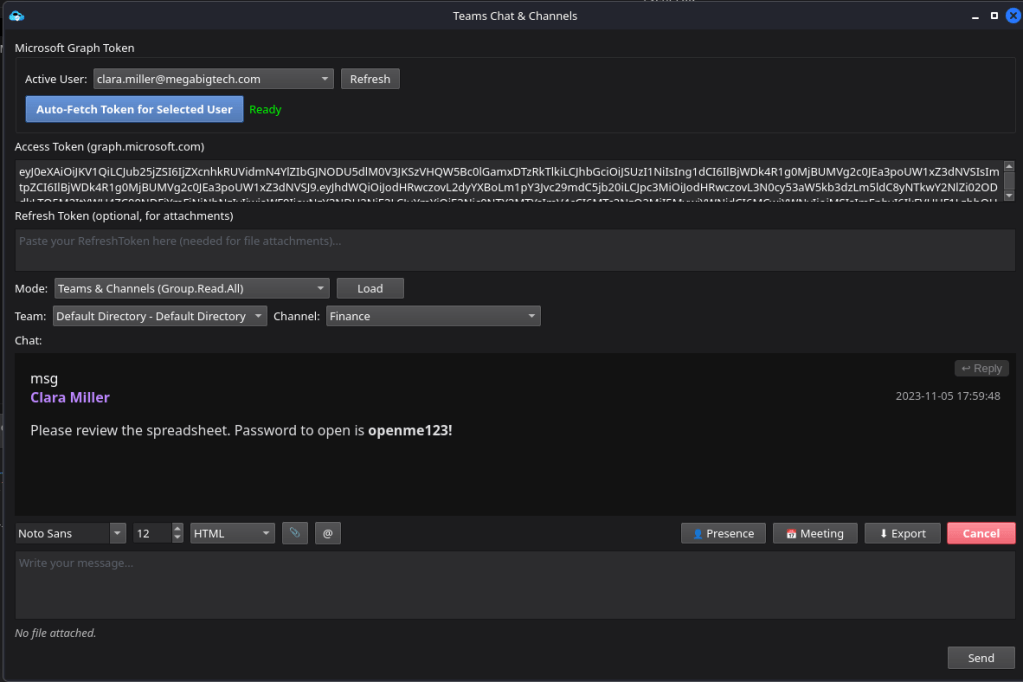
Based on the privileges associated with our token, we currently have limited permissions that allow read only access to Microsoft Teams chats. While certain Graph endpoints, client identifiers, and additional scopes would permit direct interaction and message replies, those capabilities are not available within the scope of our current access.
We open and view all files with interesting data, but we move onto viewing the current users Inbox.
By browsing the user mailbox, we identify relevant information within the Sent Items folder.
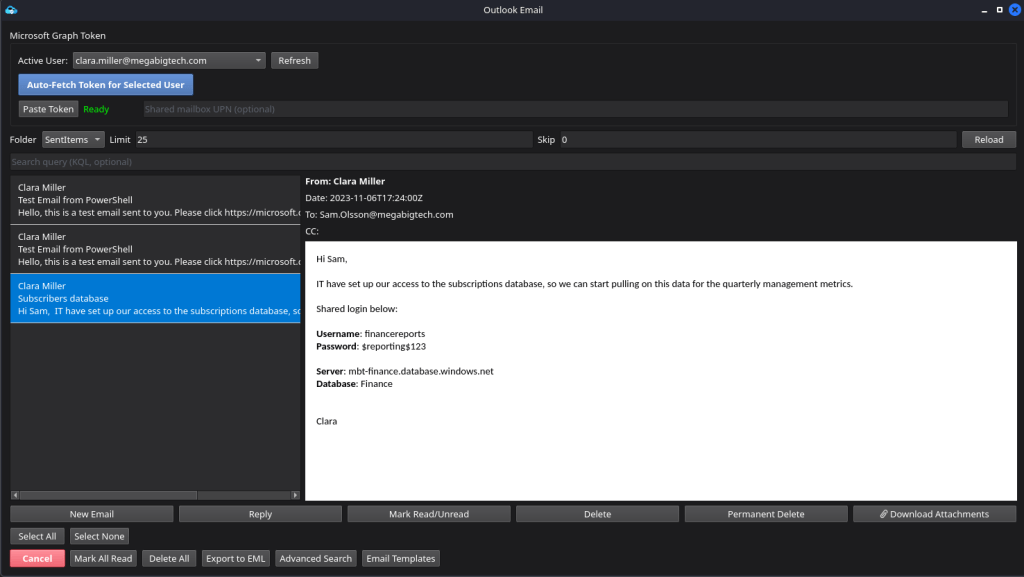
With these credentials we can Access the Database and find PII which leads us to the final flag.
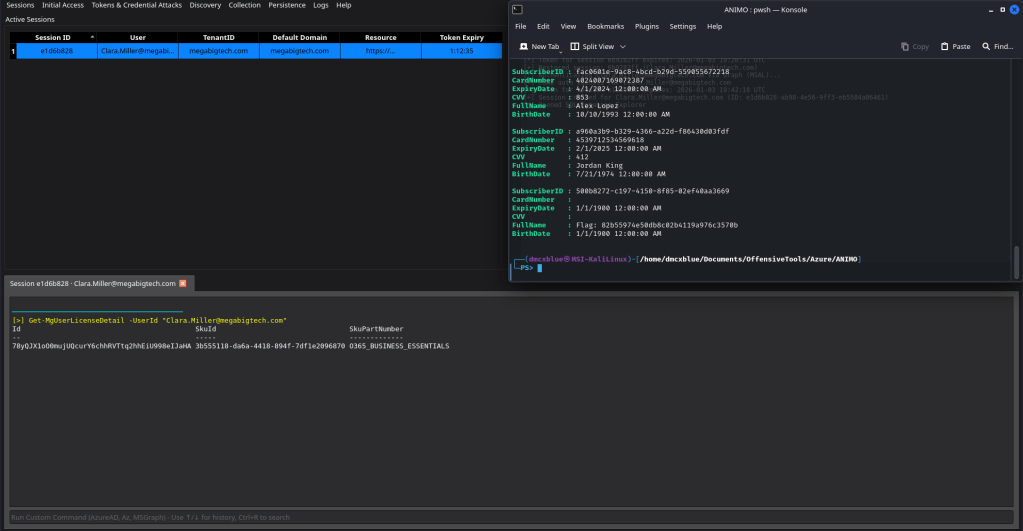
ANIMO enables us to complete the engagement with minimal reliance on multiple external tools. Its interface supports efficient navigation, automated handling and population of required tokens, and streamlined execution of common operational scenarios. That said, a deeper analysis of its capabilities is warranted. ANIMO has several modules some focus specifically on Initial Access and Persistence, and we will examine a selection of these to better understand their operational value.
Initial Access
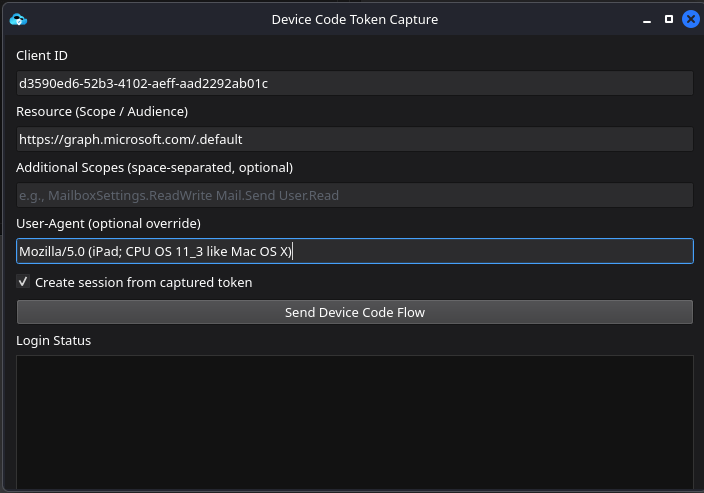
Device Code Phishing has become a popular technique for achieving Initial Access by compromising the target token and its associated level of access. This method is highly effective because it leverages legitimate Microsoft services, workflows, and authentication requests to facilitate the compromise. ANIMO further enhances this approach by allowing detailed customization of how the request is generated and delivered, including selection of the Client ID, User-Agent which is particularly relevant for Conditional Access policy evasion, requested scopes, and the target resource URL. Given its reliability and flexibility, it remains a primary technique used by Red Team operators.
Now ANIMO has a simple interface that asks you to fill in the necessary values, once these are populated you will receive your Device Code Link and you can start phishing with it, the framework will poll for any tokens every 5 seconds until failure, since we know that phishing can be extended to multiple people ANIMO also handles multiple device code links to handle multiple targets at once.
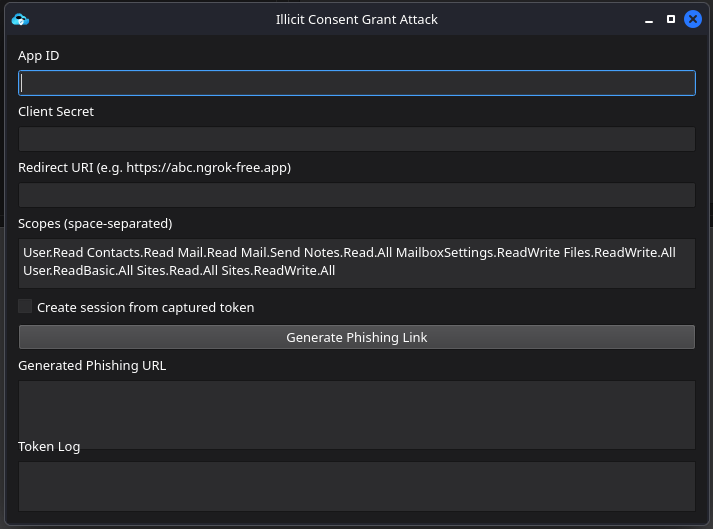
Another technique for Initial Access is Illicit Consent Grant. Based on prior operational experience, this technique has traditionally required deliberate setup and careful configuration, with only a limited number of tools available to support it.
The preparation phase often introduces friction and increases time to execution. To address this, the objective is to automate as much of the setup process as possible, allowing the attack to be staged and ready for use with minimal overhead. Some manual configuration remains necessary, including registering a rogue application, generating a client secret, and configuring a redirect URI to ensure proper functionality. Fortunately, these steps are straightforward and can be completed quickly.
Persistence
ANIMO provides several well known persistence techniques in a seamless manner. Current options include Add to Group, Backdoor App, SPN Secrets, Role Assignments, and Invite Guest. These techniques enable an operator to establish persistence within an Azure tenant. OPSEC security ultimately depends on the experience and judgment of the operator. ANIMO does, however, provide guidance by outlining the required scopes, applicable resource URLs, and relevant considerations for each technique.

Final Thoughts
With a wide range of post exploitation modules spanning Persistence and Discovery, ANIMO enables access to multiple Microsoft 365 resources. These include SharePoint, Outlook email and calendar data, Microsoft Teams messages, and internal SharePoint sites containing files shared through Teams, as well as sent, received, and draft emails. These capabilities provide visibility into both routine user activity and higher value organizational assets.
That said, ANIMO still has areas that require further development. The objective is to deliver a finished and stable project suitable for broader release. If achieved, it has the potential to become a valuable asset for cybersecurity engineers operating in the offensive space, while also offering defensive teams clear insight into the extent of access a single compromised token can provide across an enterprise environment.